
Over the last weeks, Kaspersky detected a series of sophisticated attack attempts aimed at deceiving an organization’s finance team into paying fraudulent invoices. Emails mimicking correspondence between the organization’s CEO and contractor companies were sent to the organization’s finance department to persuade them into paying urgent “invoices” for alleged “consulting services”. These attack attempts highlight a disturbing trend of targeted schemes leveraging forged executive identities to exploit corporate trust.
The analyzed attack attempts were examples of business email compromise (BEC) attacks. As a rule, such attacks are made on behalf of a management representative of a compromised firm. Importantly, in all analyzed cases the senders were fake – the real addresses from where the emails came had nothing in common with the displayed sender names. These tricks were used to persuade the victims that the emails were legitimate.
Some incidents involved emails that imitated correspondence between the company’s CEO and an alleged contractor law firm, urging the financial department to pay the attached fake invoice. The fake correspondence with the CEO of a victim company was used as “proof” that the request for payment was legitimate. In this attack the name of the fictional partner company was indicated only in the name of the sender field, and a real email address was different and changed from email to email.
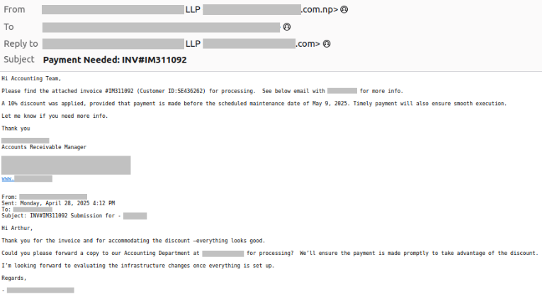
Other incidents featured similar emails that mimicked communications between the CEO and contractor companies to request urgent payment for a fake invoice, but this time the invoice itself was not attached.
“This attack stands out for its meticulous attention to detail and exploitation of trusted relationships. By fabricating convincing email threads and impersonating high-level executives, attackers are banking on employees’ reluctance to question seemingly authentic requests. Companies must prioritize employee training and robust email verification systems to counter these evolving threats,” commented Anna Lazaricheva, spam analyst at Kaspersky.
In order to avoid becoming a victim of fraudulent messages and specifically business email compromise attacks, Kaspersky experts advise the following: Check the sender’s email address and do not rely on the displayed name of the sender, as actual email addresses may have nothing in common with the companies and people who are displayed to have sent the email. Only open emails and click links if you are sure you can trust the sender; make sure that the sender’s address is legitimate.
When a sender is legitimate, but the content of the message seems strange, it is worth checking with the sender via an alternative means of communication. Check the spelling of a website’s URL if you suspect you are faced with a phishing page. The URL may contain mistakes that are hard to spot at first glance, such as a 1 instead of I or 0 instead of O. Use a proven security solution when surfing the web.



